在TKE集群部署kubernetes-dashboard服务 具体参考
基于已经创建好的Kubernetes集群进行部署Kubernetes-dashboard
下载部署yaml文件 wget https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.4/aio/deploy/recommended.yaml
下载镜像 由于镜像是国外镜像,国内集群部署有可能会拉取镜像失败,可以先手动拉取下来,然后修改对应的yaml文件
docker pull kubernetesui/dashboard:v2.0.4
访问方式配置(可选) 对应的service 默认是clusterIP方式,如果需要CLB去访问 或者nodePort方式去访问,可以修改对应的yaml文件,也可以部署完后修改
kind: Service apiVersion: v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard spec: ports: - port: 443 targetPort: 8443 selector: k8s-app: kubernetes-dashboard type: NodePort
部署kubernetes-dashboard kubectl apply -f recommended.yaml
查看是否部署成功
[root@VM-249-41-tlinux ~]
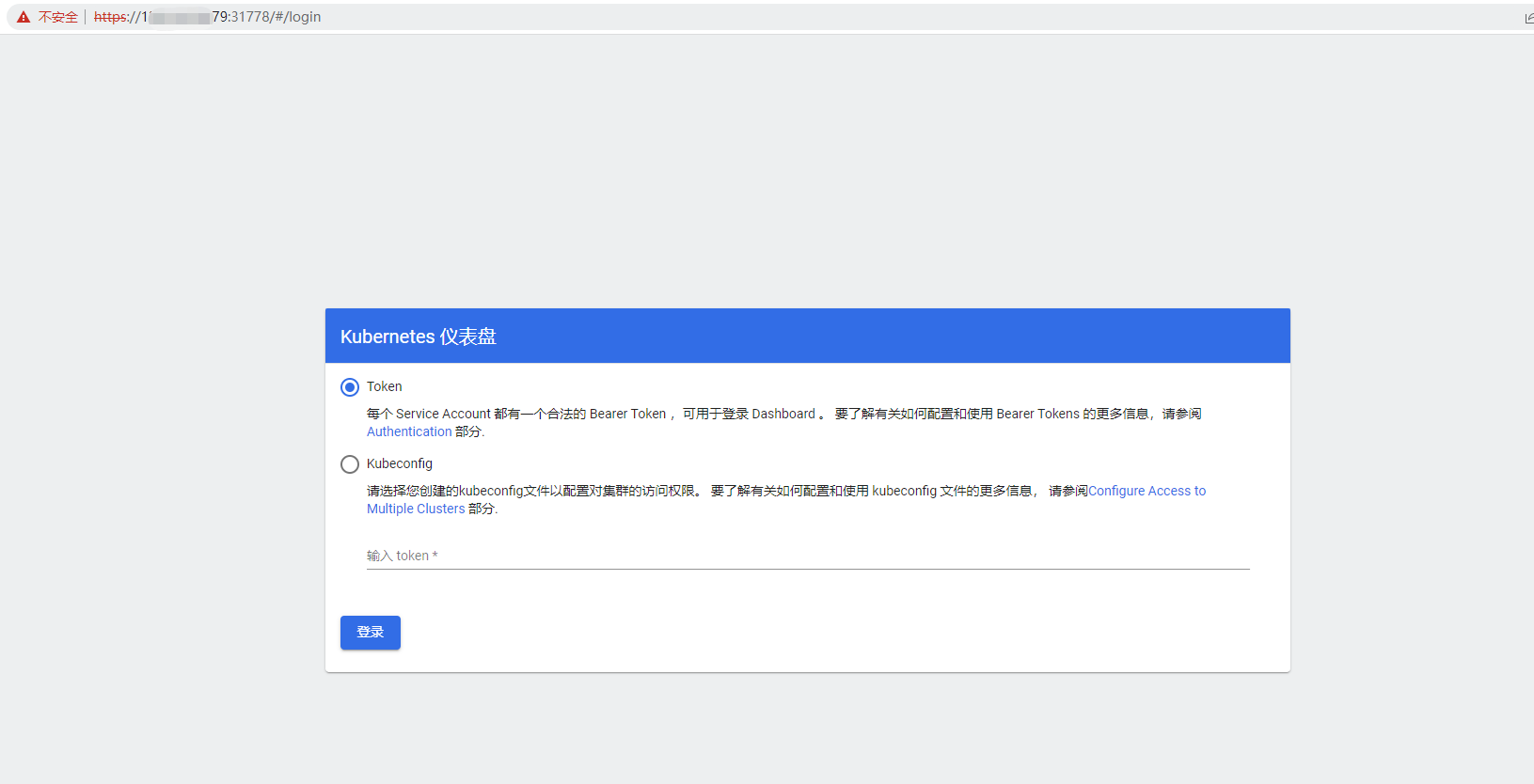
访问kubernetes-dashboard 由于上面service使用的是NodePort类型,可以通过nodeIP+NodePort端口去访问,kubernetes-dashboard后端服务是https协议的,则需要通过https://节点IP:NodePort
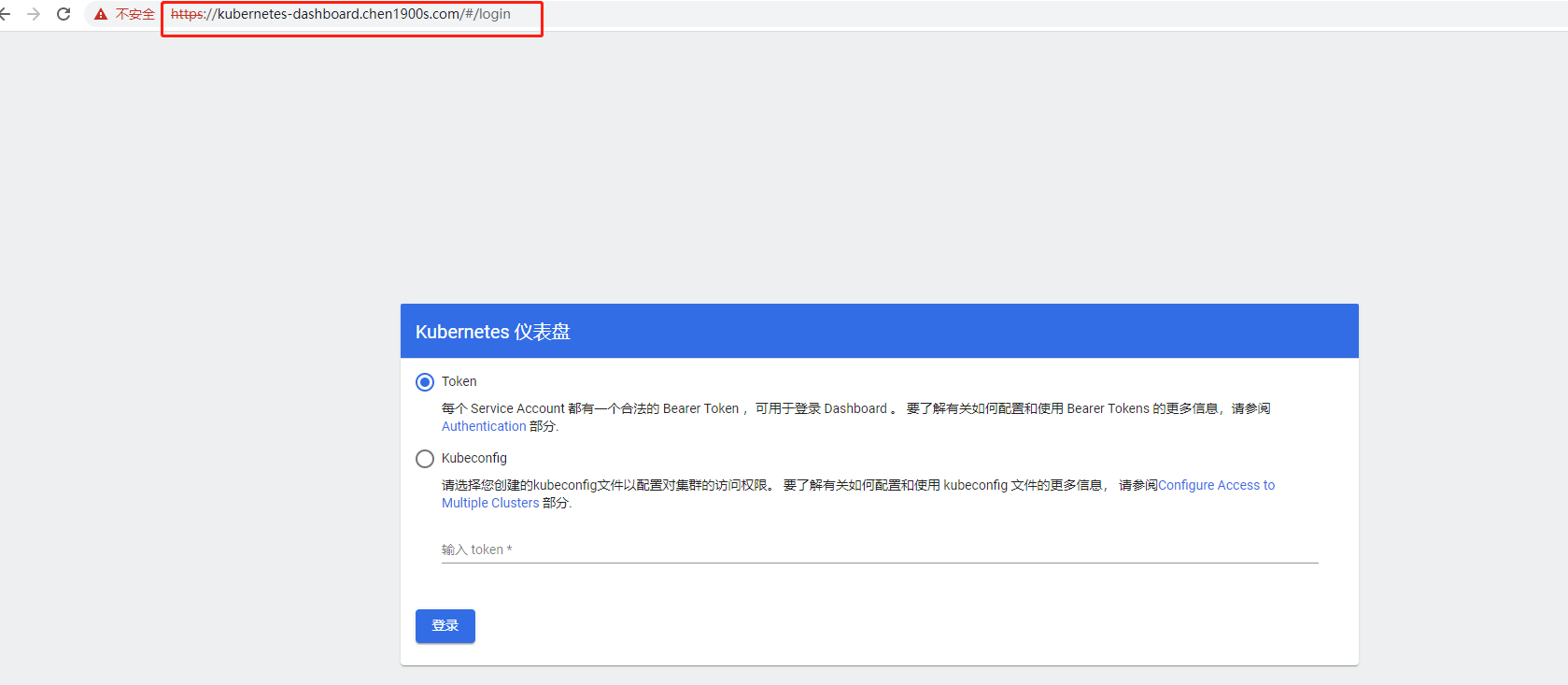
验证方式选择token
TKE集群获取Token认证方式 # 创建serviceaccount
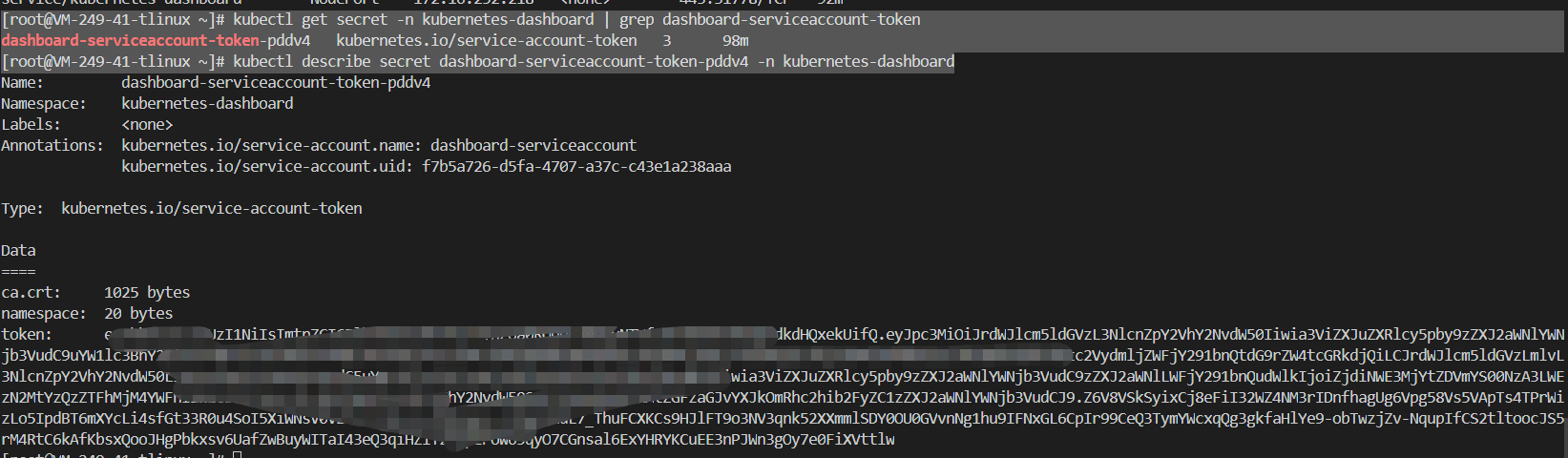
获取token
[root@VM-249-41-tlinux ~]# kubectl get secret -n kubernetes-dashboard | grep dashboard-serviceaccount-token
复制token 到控制台
基于Istio的访问kubernetes-dashboard配置 参考istio官方文档
前提条件:
1,服务网格已经关联集群
2,已经创建边缘代理网关istio-ingressgateway
首先需要开启 Sidecar 自动注入配置,命名空间选择kubernetes-dashboard,然后销毁重建kubernetes-dashboard的POD
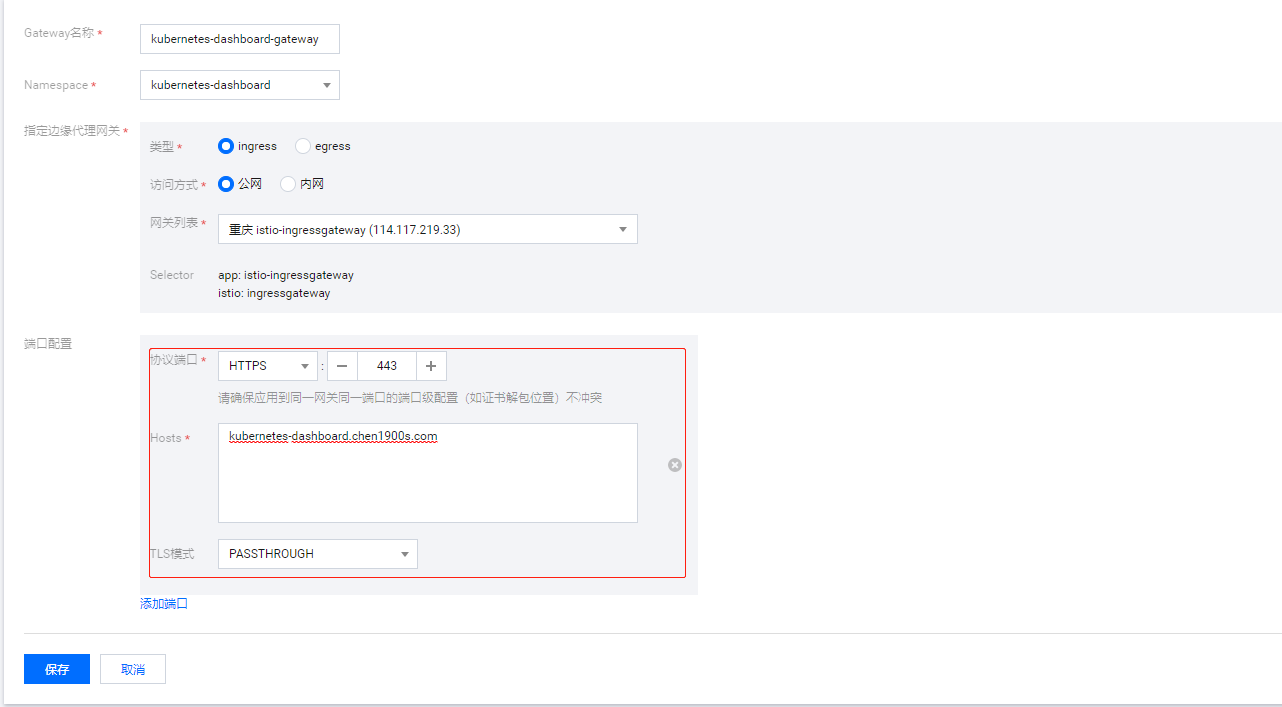
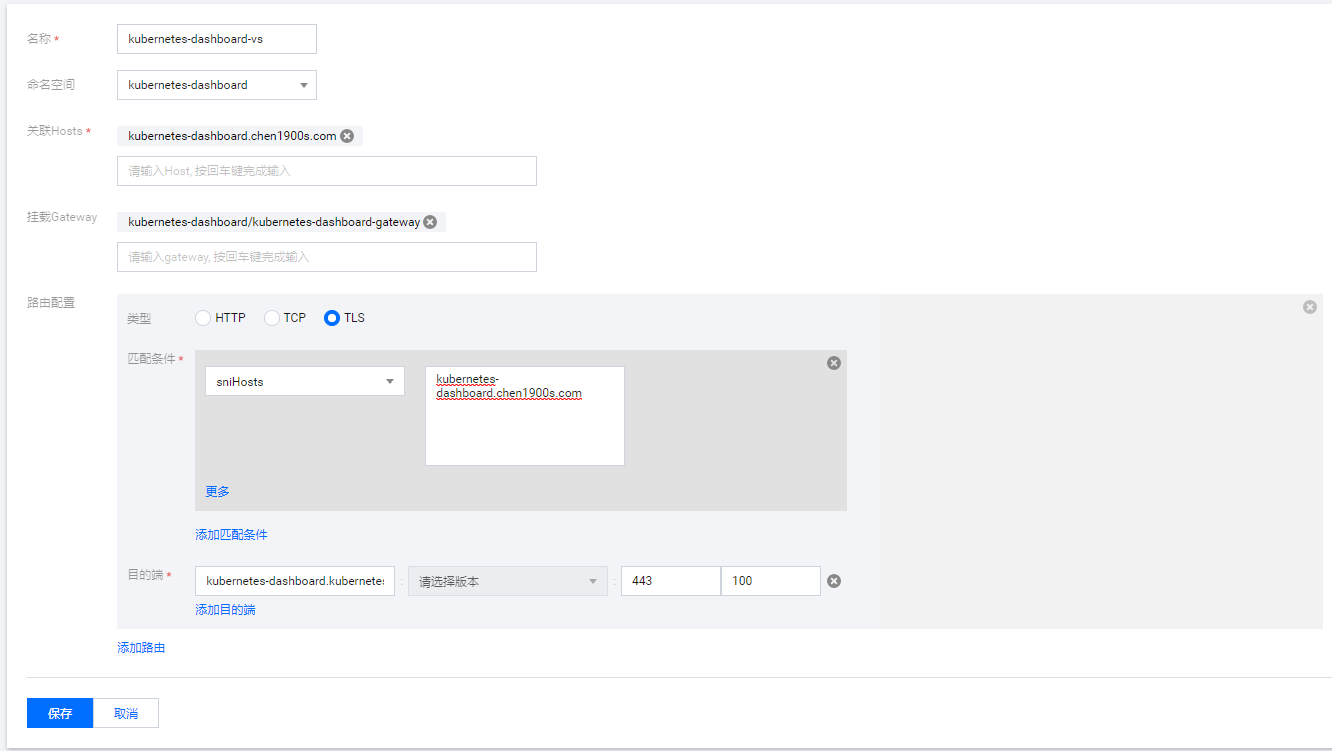
新建Gateway 这里使用自定义的域名kubernetes-dashboard.chen1900s.com
对应yaml:
apiVersion: networking.istio.io/v1alpha3
创建Virtual Service
yaml文件
apiVersion: networking.istio.io/v1alpha3
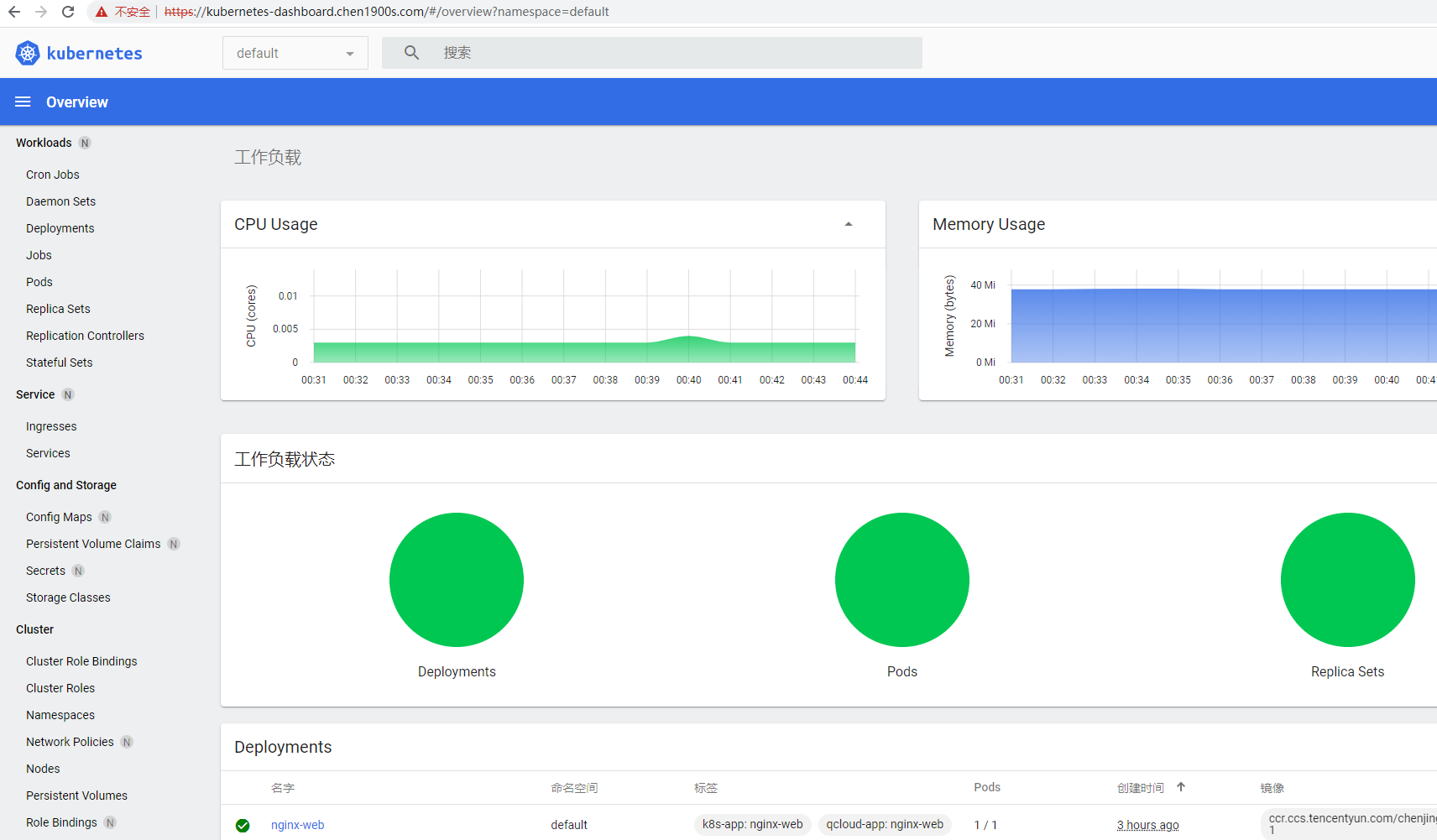
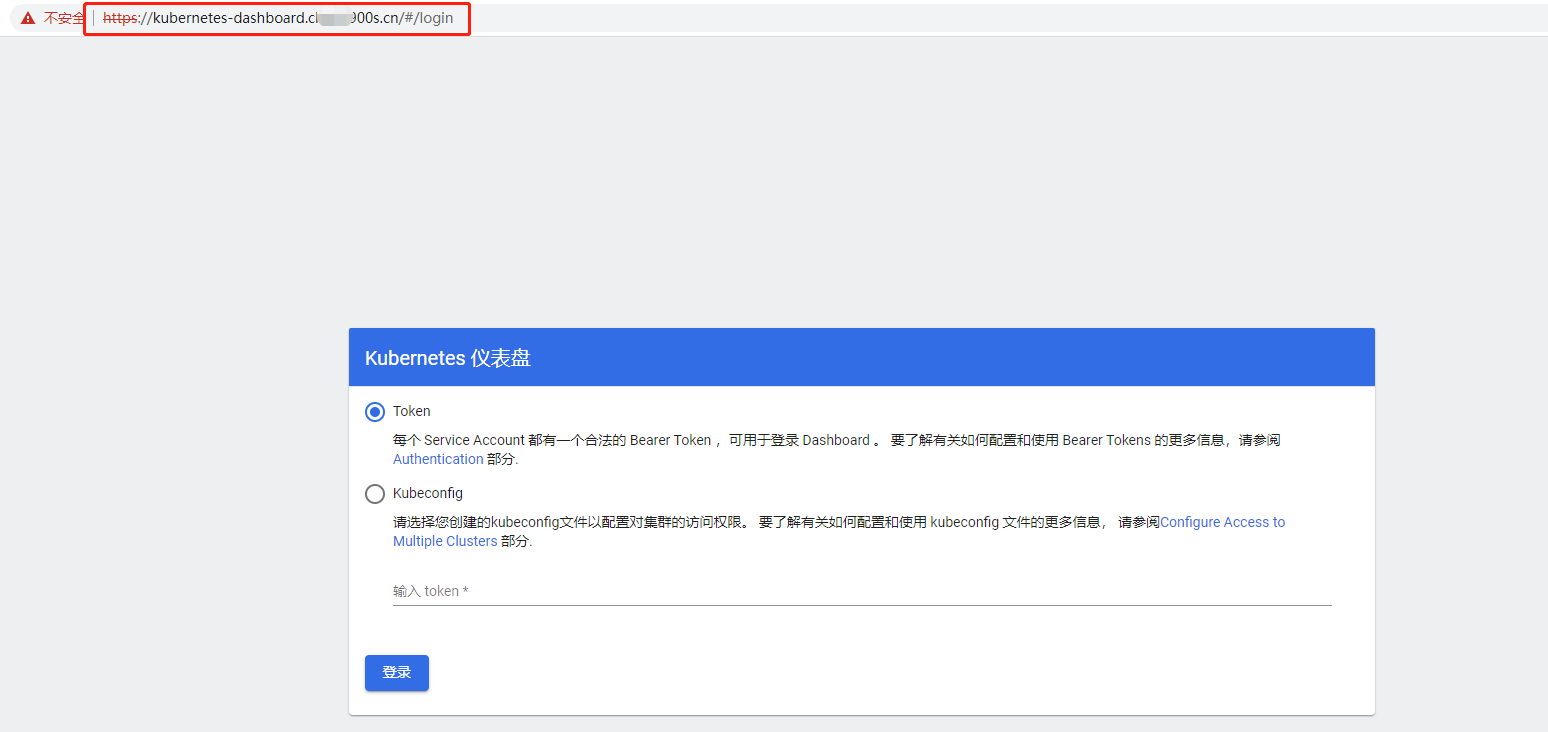
设置完成后,配置如下本地host映射,即可通过域名 https://kubernetes-dashboard.chen1900s.com 访问,效果与之前的NodePort一致
[root@VM-249-41-tlinux ~]# kubectl -n istio-system get svc istio-ingressgateway
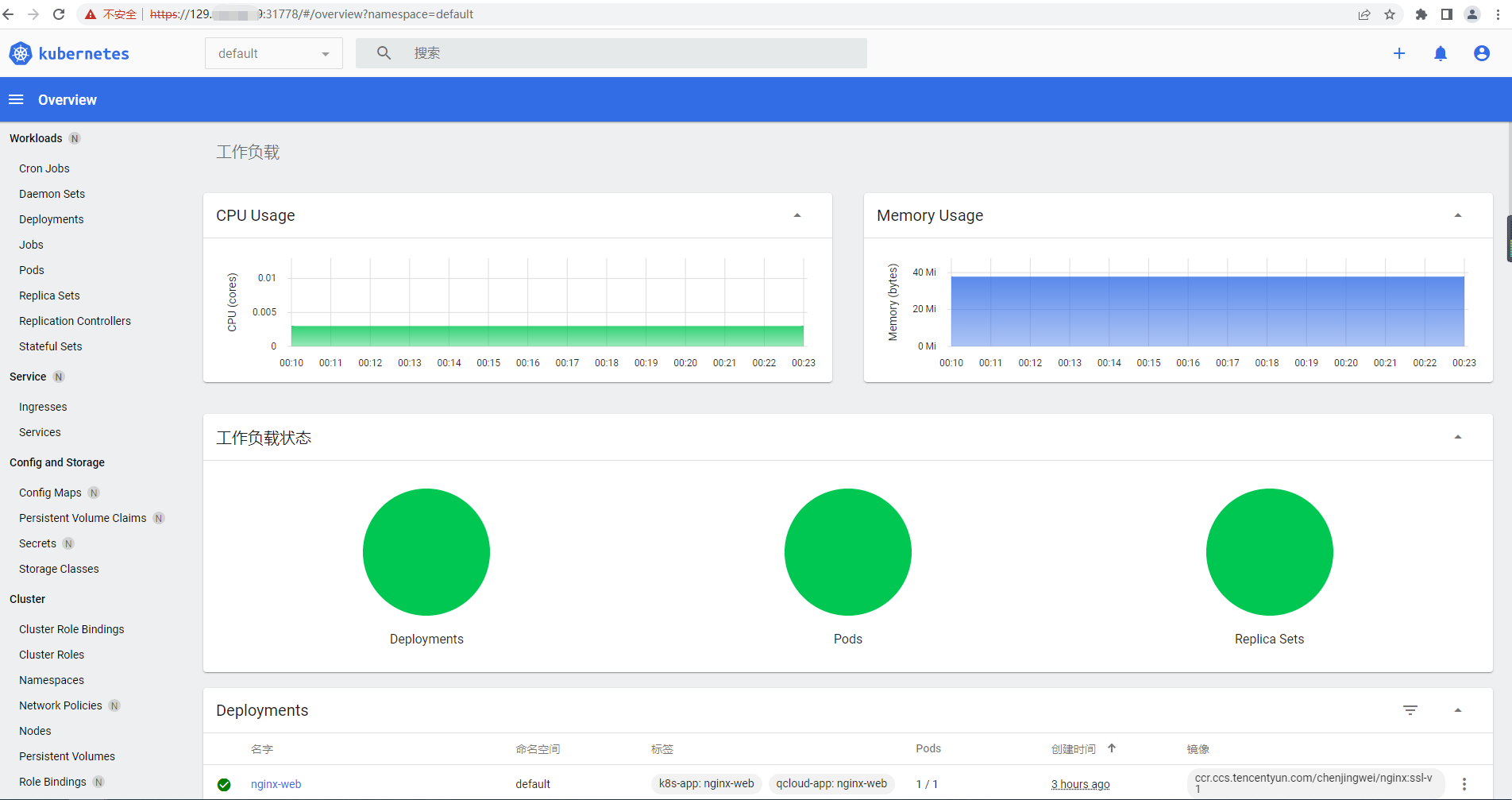
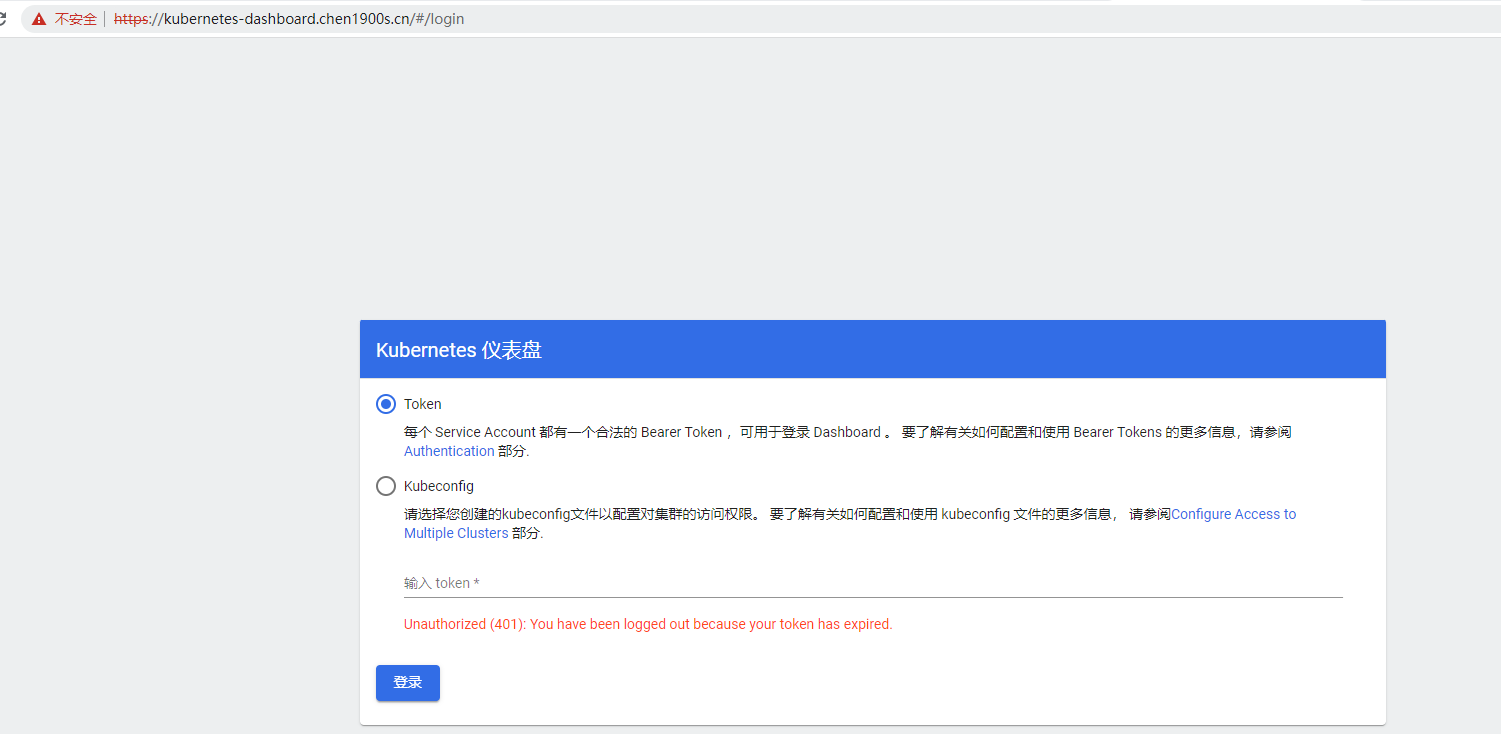
输入上面查询到的token 可以正常登陆
Istio中基于Secure Ingress的访问方式还有多种
基于nginx-ingress方式访问kubernetes-dashboard Nginx Ingress Controller默认使用HTTP协议转发请求到后端业务容器。当后端业务容器为HTTPS协议时,可以通过使用注解nginx.ingress.kubernetes.io/backend-protocol: "HTTPS"来使得Nginx Ingress Controller使用HTTP协议转发请求到后端业务容器
kubernetes-dashboard服务正是HTTPS协议服务,则需要使用这个annotations
环境准备:
1,已经创建nginx-ingress-controller 实例
2,已经创建TLS证书
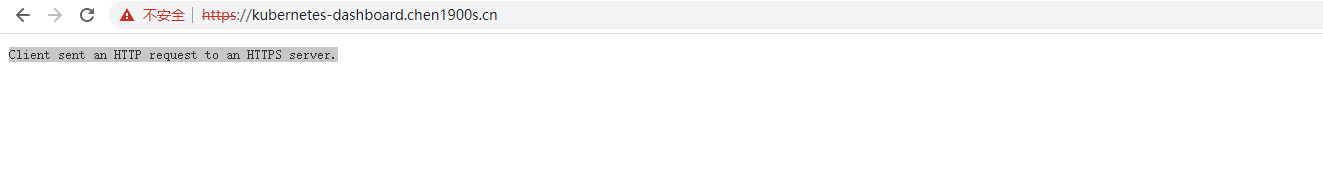
首先是如果不添加这个annotations 访问会报 Client sent an HTTP request to an HTTPS server.
添加nginx.ingress.kubernetes.io/backend-protocol: “HTTPS” 后访问正常
yaml文件:
apiVersion: networking.k8s.io/v1beta1 kind: Ingress metadata: annotations: kubernetes.io/ingress.class: nginx kubernetes.io/ingress.rule-mix: "true" nginx.ingress.kubernetes.io/backend-protocol: HTTPS nginx.ingress.kubernetes.io/use-regex: "true" name: kubernetes-dashboard namespace: kubernetes-dashboard spec: rules: - host: kubernetes-dashboard.chen1900s.cn http: paths: - backend: serviceName: kubernetes-dashboard servicePort: 443 path: / pathType: ImplementationSpecific tls: - hosts: - kubernetes-dashboard.chen1900s.cn secretName: chen1900s
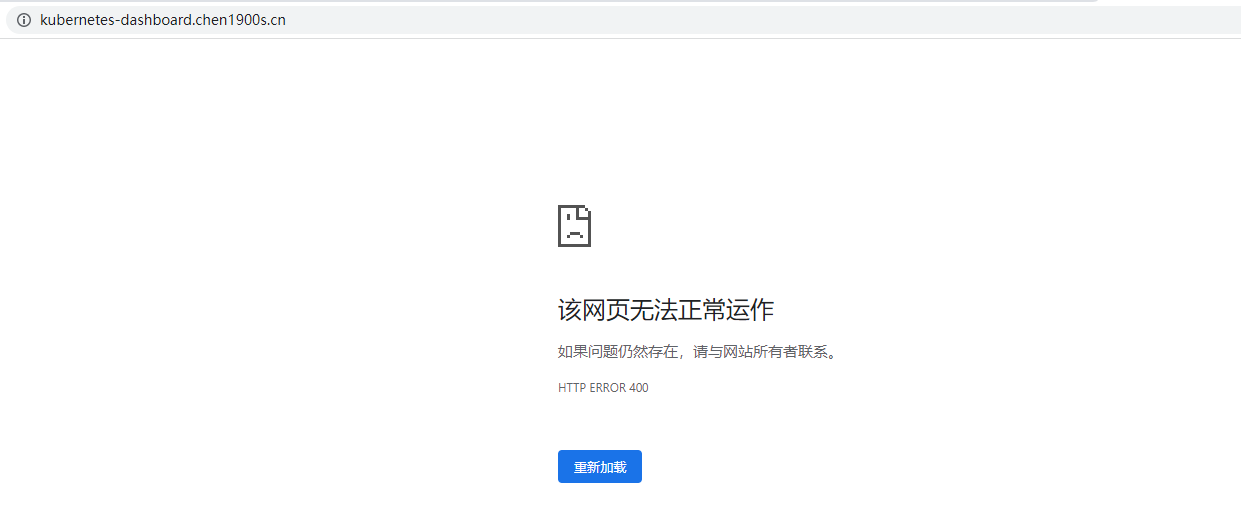
基于CLB类型ingress方式访问kubernetes-dashboard配置 CLB类型ingress,对应后端服务协议是默认HTTP的,后端协议是指 CLB 与后端服务之间协议,后端协议选择 HTTP 时,后端服务需部署 HTTP 服务。后端协议选中 HTTPS 时,后端服务需部署 HTTPS 服务,HTTPS 服务的加解密会让后端服务消耗更多资源
如果需要后端协议为HTTPS 则需要使用TkeServiceConfig来配置ingress自动创建的CLB
如果不通过TkeServiceConfig配置后端是HTTPS服务时候,访问会异常,如下:
使用 TkeServiceConfig 配置 CLB 创建 Ingress 时,设置 ingress.cloud.tencent.com/tke-service-config-auto: ,将自动创建 -auto-ingress-config
apiVersion: networking.k8s.io/v1beta1 kind: Ingress metadata: annotations: ingress.cloud.tencent.com/tke-service-config-auto: "true" kubernetes.io/ingress.class: qcloud kubernetes.io/ingress.rule-mix: "true" name: kubernetes-dashboard namespace: kubernetes-dashboard spec: rules: - host: kubernetes-dashboard.chen1900s.cn http: paths: - backend: serviceName: kubernetes-dashboard servicePort: 443 path: / pathType: ImplementationSpecific tls: - hosts: - kubernetes-dashboard.chen1900s.cn secretName: chen1900s-ye4ubdzo
查看TkeServiceConfig配置
[root@VM-249-41-tlinux ~]
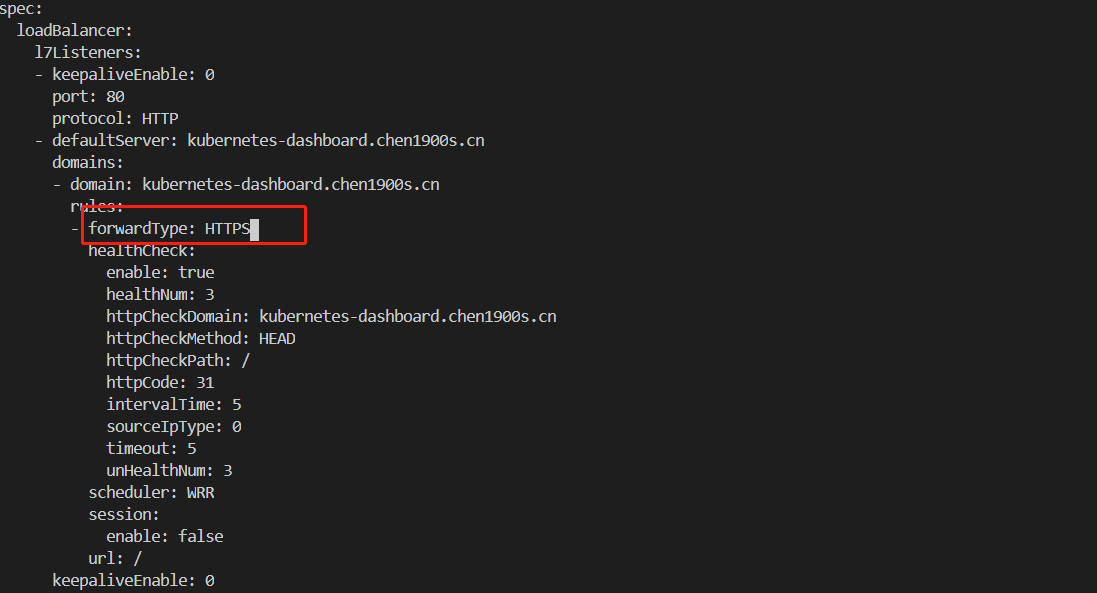
编辑这个配置文件,修改后端协议 spec.loadBalancer.l7listeners.protocol.domain.rules.url.forwardType: 指定后端协议
kubectl -n kubernetes-dashboard edit TkeServiceConfig kubernetes-dashboard-auto-ingress-config
然后使用这个CLB对应的域名进行访问
附:
apiVersion: cloud.tencent.com/v1alpha1 kind: TkeServiceConfig metadata: name: kubernetes-dashboard-auto-ingress-config namespace: kubernetes-dashboard spec: loadBalancer: l7Listeners: - defaultServer: kubernetes-dashboard.chen1900s.cn domains: - domain: kubernetes-dashboard.chen1900s.cn rules: - forwardType: HTTPS healthCheck: enable: true healthNum: 3 httpCheckDomain: kubernetes-dashboard.chen1900s.cn httpCheckMethod: HEAD httpCheckPath: / httpCode: 31 intervalTime: 5 sourceIpType: 0 timeout: 5 unHealthNum: 3 scheduler: WRR session: enable: false url: / keepaliveEnable: 0 port: 443 protocol: HTTPS - keepaliveEnable: 0 port: 80 protocol: HTTP